Welcome to EcoOnline ePermits
Unfortunately, this product isn't available outside of UK and Ireland. If you’re looking for a simple EHS solution for your organization, explore our Health & Safety Software. Our customizable platform enables you to effectively manage all your H&S needs in one place.
*Contact a member of our team for a solution that fits your needs and location.
Permit to Work Software
Automated approval workflows reduce admin, whilst visibility of work permits anywhere at anytime prevents compliance gaps.
“The beauty of the system is how instantly you can review permits. If a person is seen on site, and they are questioned about what they are there to do, and they haven’t got an issued permit, they are removed from site. This protects us and them.”
St George's Hospital
9,000 permits a month
Our customers generate 9,000 permits a month, whilst saving hours of time. Automated approval workflows reduce admin, whilst visibility of work permits anywhere at anytime, prevents compliance gaps. With evidence stored in one place, you get a robust audit trail you can trust.
Take control of the 4 permit stages
Digitally transform your
permit-to-work process
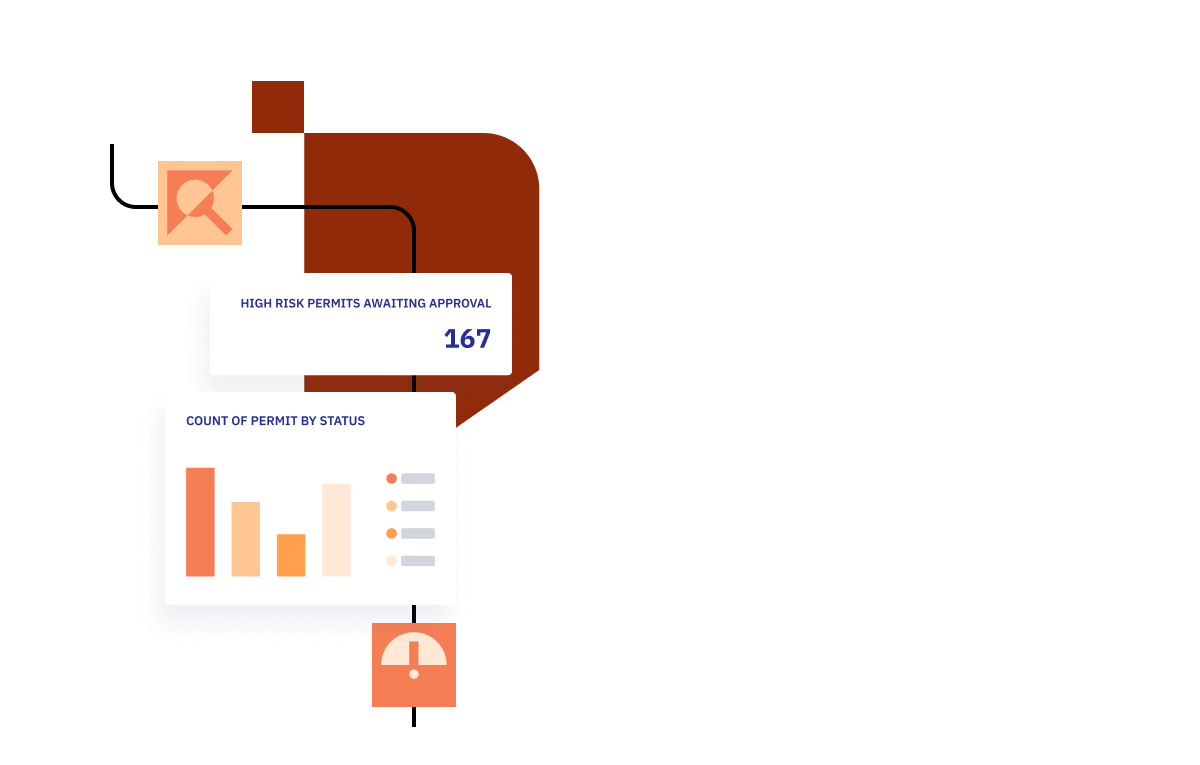
- Reduce human error.
- Mitigate risk with full contractor and worker control.
- Gain time thanks to faster, more efficient reporting.
- Automate workflows, audits and alerts.
- Collect evidence for audits in one place.
- Quick-to-learn, user-friendly software.
Getting started is simple
Fill out the contact form
We’ll be in touch in the next 24-48 hours on weekdays to schedule a chat with one of our consultants.
Your personalised guided tour
You’ll get concierge-level service, with a customised tour to demonstrate how our software can help.
Start your journey towards a safer workplace
Discover how simple EHS can be when you’ve found the right solution for your organisation.
Key Features

100% digital, paperless process.

Insurance and certification checks with fast e-signatures.
Insurance checks, Asbestos management and Supply chain management.

Follow the process from request to closed

No stone left unturned with automated checks and notifications.
Permits-to-work
Sanctions to test
PPE Selection
Electronic signatures

RAMS management and RAMS assessment.
Frequently asked questions
What sectors is ePermits suitable for?
ePermits is optimized for property management, finance, retail, insurance, research, technology, public administration, heritage, and commercial real estate. Additionally, we have customers in healthcare and manufacturing.
Who keeps the training records up to date when using ePermits?
Many thousands of companies keep their health and safety competence records up to date using the ePermits database. If any companies in your supply chain are not already using the system, they would have access to a self-help section and training within the application to input the necessary data themselves.
What permit templates does ePermits generate?
There are 16 permit types reflecting the different tasks which contractors may need to undertake with the ability to add safety precautions or custom fields to align to specific requirements.
Who implements ePermits?
The ePermits by EcoOnline experienced team will implement the system for you. We only require you to be available for discovery workshops and training.
Who provides the training for ePermits?
The ePermits by EcoOnline provide remote training in English for clients, Authorised Persons and their supply chains. We will also provide enhanced user training for system super users.
Who hosts the ePermits system?
ePermits is delivered to clients through a Software as a Service (“SaaS”) model in which the application is hosted physically remotely from client sites within a data centre and accessed through web pages delivered to the user via a standard web browser.
EcoOnline's hosting partner is Microsoft Azure, one of the world leading cloud hosting providers. EcoOnline works closely with Azure to ensure that the hosting infrastructure meets the needs of our clients, has appropriate levels of security in place and has the ability to be maintained, scaled and upgraded with minimal, if any, impact to clients.
What hardware is required to run ePermits?
Does ePermits work on mobile devices?
Yes, ePermits will operate its full functionality on most phones and tablet devices.
What browsers does ePermits support?
The latest versions of Edge, Firefox, Chrome and Safari.
Your journey towards a safer workplace starts with a chat.
When you speak with one of our in-house EHS experts, you’ll discover the exact software modules that will help streamline your organisation’s current Health & Safety processes. Save time and grow a positive safety culture with the help of intuitive EHS software.
Book a demo of our software

Trusted by 10,000+ customers worldwide
With the knowledge from 90 different industries we have developed our platform to make sure it tailors to your needs.
Don't take our word for it.




Save even more time when you bundle your EHS solutions
Practice the best chemical safety and compliance with a cloud-based platform your employees can use from anywhere.
Reduce time-consuming health and safety training paperwork with a customisable digital learning platform.
Get a clear picture of your environmental performance data with tools that make it easier to turn insights into positive actions.


